Why Do Organizations Need Secure Development Environments?
The need to secure corporate IT environments is common to all functions of organizations, and software application development is one of them.
At its core, the need for securing IT environments in organizations arises from the digital corporate assets that they carry. It’s often data attached to privacy concerns, typically under regulations such as GDPR or HIPAA, or application source code, credentials, and most recently operational data that can have strategic significance. In the case of environments for software application development, the complexity of the security problem lies in addressing the diversity of these environments’ settings. They range from data access needs and environment configuration to the developer’s relationship with the company, e.g. internal employee, consultant, temporary, etc.
Security left aside, development environments have notoriously complex setups and often require significant maintenance because many applications and data are locally present on the device’s internal storage, for example the integrated development environment (IDE) and the application’s source code.
Hence, for these environments data protection against leaks will target locally stored assets, i.e. source code, credentials, and potentially sensitive data.
Assessing the Risk of Locally Stored Data
In 2010, the use of the Cloud as a storage medium for corporate data was nascent, hence today, the metrics to determine the cost and impact of the loss of a corporate laptop would likely look very different.
For example, for many of the business functions that were likely to be impacted at that time, Cloud applications have brought today a solution by removing sensitive data from employees’ laptops. This has mostly shifted the discussion on laptop security to protecting the credentials required to access Cloud (or self-hosted) business resources, rather than protecting locally stored data itself.
There is, though, a notable exception to the above shift in technology: the environments used for code development. For practical reasons, devices used for development today have a replica of projects’ source code, in addition to corporate secrets such as credentials, web tokens, cryptographic keys and perhaps strategic data to train machine learning models or to test algorithms.
In other words, there is still plenty of interesting data stored locally in development environments that warrant protection against loss or theft. Therefore, the interest in securing development environments has not waned.
There are a variety of reasons for malicious actors to go after assets in these environments, from accessing corporate intellectual property (see the hack of Grand Theft Auto 6), to understanding existing vulnerabilities of an application in order to compromise it in operation. Despite all these potential downfalls resulting from the hacking of a single developer’s environment, few companies today can accurately determine where the replicas of their source code, secrets and data are (hint: likely all over the devices of their distributed workforce), and are poorly shielded against the loss of a laptop or a looming insider threat. Recall that, using any online or self-hosted source code repositories such as GitHub does not get rid of any of the replicas in developers’ environments. This is because local replicas are needed for developers to update the code before sending it back to the online Git repository. Hence protecting these environments is a problem that grows with the number of developers working in the organization.
Use Cases for Virtual Desktops and Secure Developer Laptops
The desire to remove data from developers’ environments is prevalent across many regulated industries such as Finance and Insurance. One of the most common approaches is the use of development machines accessed remotely.
Citrix and VMware have been key actors in this market by enabling developers to remotely access virtual machines hosted by the organization. In addition, these platforms implement data loss prevention mechanisms that monitor user activities to prevent data exfiltration. Running and accessing a virtual machine remotely for development has many drawbacks in particular on the developer’s productivity. One reason is because the streaming mechanism used to access the remote desktop requires significant bandwidth to be truly usable and often results in irritating lags when typing code.
The entire apparatus is also complex to set up as well as costly to maintain and operate for organization. In particular, the use of a virtual machine is quite a heavy mechanism which requires significant computational resources (hence cost) to run.
Finally, such a set-up is general-purpose, i.e. it is not designed in particular for code development and requires the installation of the entire development tool suite.
For the reasons explained above, many organizations have reverted to securing developer laptops using end-point security mechanisms implementing data loss prevention measures. In the same way as for the VDI counterpart, this is also often a costly solution because such laptops have complex setups. When onboarding remote development teams, organizations often send these laptops through the mail at great expense, which complicates the maintenance and monitoring process.
The Case for Secure Cloud Development Environments
Recently, virtualization has evolved from emulating entire machines to the granularity of single processes with the technology of software containers. Containers are well-suited for code development because they provide a minimal and sufficient environment to compile typical applications, in particular web-based ones. Notably, in comparison to virtual machines, containers start in seconds instead of minutes and require much fewer computational resources to execute. Containers are typically a tool used locally by developers on their devices to isolate software dependencies related to a specific project in a way that the source code can be compiled and executed without interference with potentially unwanted settings.
The great thing about containers is that they don’t have to remain a locally used development tool. They can be run online and used as an alternative to a virtual machine. This is the basic mechanism used to implement a Cloud Development Environment (CDE). Running containers online has been one of the most exciting recent trends in virtualization aligned with DevOps practices where containers are critical to enable efficient testing and deployments. CDE are accessed online with an IDE via network connection (Microsoft Visual Studio Code has such a feature as explained here) or using a Cloud IDE (an IDE running in a web browser such as Microsoft Visual Studio Code, Eclipse Theia and others.) A Cloud IDE allows a developer to access a CDE with the benefit that no environment needs to be installed on the local device. Access to the remote container is done transparently. Compared to a remotely executing desktop as explained before, discomfort due to a streaming environment does not apply here since the IDE is executing as a web application in the browser. Hence the developer will not suffer display lags in particular in low bandwidth environments as is the case with VDI and DaaS. Bandwidth requirements between the IDE and the CDE are low because only text information is exchanged between the two.
As a result, in the specific context of application development, the use of CDEs is a lightweight mechanism to remove development data from local devices. However, this still does not achieve the security delivered by Citrix and other VDI platforms, because CDEs are designed for efficiency and not for security. They do not provide any data loss prevention mechanism.
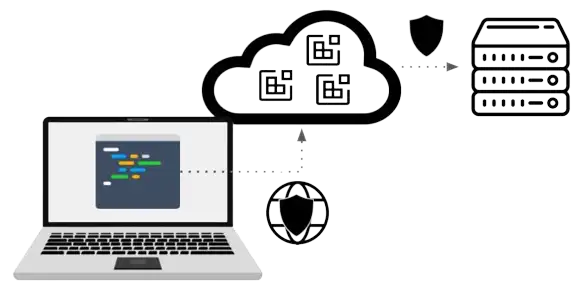
This is where the case to implement secure Cloud Development Environments lies: CDEs with data loss prevention provide a lightweight alternative to use of VDI or secure development laptops, with the additional benefit of an improved developer experience. The resulting platform is a secure Cloud Development platform. Using such a platform, organizations can significantly start to reduce the cost of provisioning secure development environments for their developers. In this additional article, I explain how such a platform is implemented. Moving From Virtual Desktops to Secure Cloud Development Environments
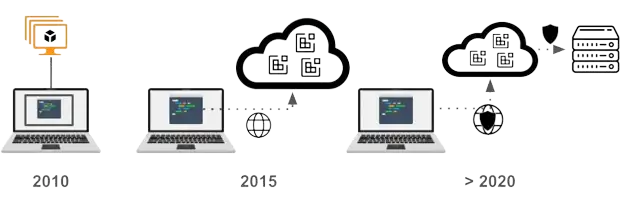
As a conclusion to this discussion, below I briefly retrace the different steps to build the case for a secure Cloud-based development platform that combines the efficient infrastructure of CDE with end-to-end data protection against data exfiltration, leading to a secure CDE. This evolution is represented in the following figure.
In the early 2010s, secure developer laptops were used to directly access corporate resources sometimes using a VPN when outside the IT perimeter. According to the benchmark study that I mentioned at the beginning of this article, 41% of laptops routinely contained sensitive data according to the study that I mentioned at the beginning of this article.
At this time, the use of virtual machines and early access to web applications has allowed organizations to remove data from local laptop storage. But code development on remote virtual machines was and remains strenuous.
Around 2015, the use of lightweight virtualization based on containers has allowed quicker access to online development environments, but the focus of platforms in this space has been primarily on productivity.
Finally, a secure Cloud Development Environment platform as shown in the rightmost part of the figure below illustrates the closest incarnation of the secure development laptop.
Secure CDEs benefit from the experiences of pioneering companies like Citrix, seizing the chance to separate development environments from traditional hardware. This separation allows for a blend of infrastructure efficiency and security without compromising developers' experience.
All material in this text can be shared and cited with appropriate credits. For more information about our platform, please contact us at hello@strong.network