Addressing Both Productivity and Security Concerns With Secure CDEs
The use of Cloud Development Environments (CDEs) allows the migration of coding environments online. Solutions range from using a self-hosted platform or a hosted service. In particular, the advantage of using CDEs with data security, i.e. Secure Cloud Development Environments (CDEs) provide the dual benefits of enabling simultaneously productivity and security.
The goal of this article is to describe and differentiate Secure CDEs with “standard CDEs” such as the ones typically found on the market as Codespaces, Google Workstation, OpenShift DevSpaces, and other smaller players on the market such as GitPod and Coder.
Strong Network is the pioneer in security for CDEs with the first platform allowing organizations to manage Secure CDEs.
Our approach to CDEs is to have a dual focus, i.e. leverage CDEs from both a productivity and security standpoint. This is in contrast to using CDEs primarily as a source of efficiency as done by the other aforementioned players. Embedding Security in CDEs allows for their deployment in Enterprise settings where security of data and infrastructure is a requirement.
Furthermore, it is possible to deliver via CDEs security mechanisms in a way that actually improves productivity as opposed to setting additional hurdles for developers. This is because these mechanisms aim at automating many of the manual security processes falling on developers in classic environments, for example the knowledge and handling of credentials.
This article is structured as follows: I first recall the typical reasons why CDEs improve productivity and efficiency. Then I explain the types of security mechanisms that Secure CDEs add to CDEs. Note that, you can also read about the fundamental differences in architecture between a CDE platform and a platform to manage Secure CDEs in this additional article: Why and How We Made Cloud Development Environments Secure. Streamline the Management Of Cloud Development Environments
Let's first consider a classic situation where developers each have the responsibility to install and manage their development environment on their devices. This is a manual, often time-consuming and local operation. In addition, jumping from one project to another will require duplicating the effort, in addition to potentially having to deal with interference between project’s specific resources.
Centralized Provisioning and Configuration
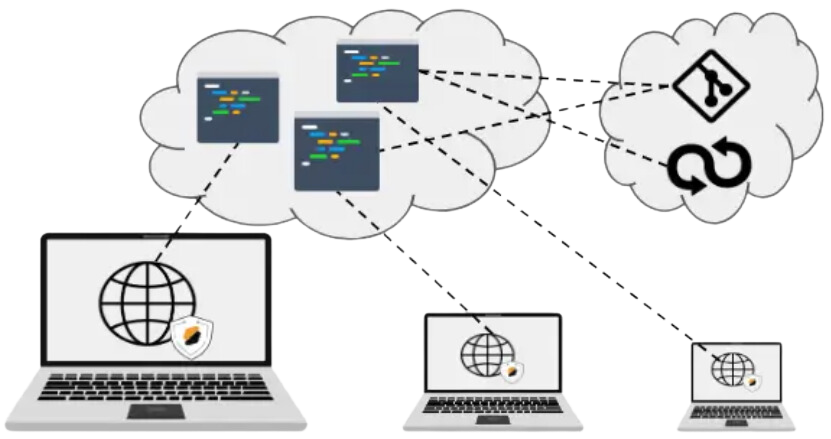
The above chore can be streamlined with a CDE managed online. Using an online service, the developer can select a development stack from a catalog and ask for a new environment to be built on demand, and in seconds. When accessing the platform, the developer can deal with any number of such environments and immediately start developing in any of them. This functionality is possible thanks to the definition of infrastructure as code, and lightweight virtualization. Both aspects are implemented with container technology. Development Resources and Collaboration
Environment definition is only one of the needs when starting a new project. The CDE platform can also streamline access to resources, from code repositories to APIs, down to the access of secrets necessary to authenticate to cloud services.
Because using a CDE platform, coding environments are managed online, it opens to the possibility for new collaboration paradigms between developers. For example, as opposed to more punctual collaboration patterns such as providing feedback on submitted code via a code repository application (i.e. via a Pull-Request), more interactive patterns become available thanks to the immediacy of using an online platform.
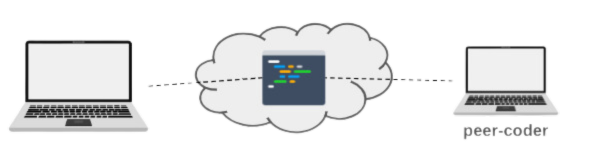
Some of the popular interactive patterns explored by vendors are peer-coding and the sharing of running applications for review.
Peer-coding is the ability to work on the same code at the same time by multiple developers. If you have used an online text editor such as Google Docs and shared it with another user for co-editing, peer-coding is the same approach applied to code development. This allows a user to edit someone else's code in her environment.
When running an application inside a CDE-based coding environment, it is possible to share the application with any user immediately. In a classic setting, this will require to pre-emptively deploy the application to another server, or share a local IP address for the local device, provided this is possible. This process can be automated with CDEs.
Cloud-Delivered Enterprise Security Using Secure CDEs
CDE are delivered using a platform that is typically self-hosted by the organization in a private cloud or hosted by an online provider. In both cases, functionalities delivered by these environments are available to the local devices used to access the service without any installation. This delivery method is sometimes referred to as Cloud-delivery. So far, we mentioned mostly functionality attached to productivity such as the management of environments, access to resources and collaborative features.
In the same manner, security features can also be Cloud-delivered yielding the additional benefit of realizing secure development practices with CDEs. From an economic perspective, this becomes a key benefit at enterprise-level because many of the security features managed using locally installing endpoint security software can be reimagined. It is our opinion that there's a great deal of innovation that can flourish by rethinking security using CDEs. This is why the Strong Network platform delivers data security as a core part of its functionalities. Why Development Data Requires Security
Most if not all companies today deliver some of their shareholders value via the development of code, the generation and processing of data, and the creation of intellectual property likely through the leverage of both aforementioned resources. Hence, the protection of the data feeding the development workforce is paramount to run operations aligned with the shareholders’ strategy..
Unfortunately, the diversity and complexity from an infrastructure perspective of the development processes often makes the protection of data an afterthought. Even when anticipated, it is often a partial initiative based on opportunity-cost considerations.
In industries such as Banking and Insurance where regulations forbid any shortcuts, resorting to remote desktops and other heavy, productivity-impacting technology is often a parsimoniously-applied solution.
When the specter of regulation is not a primary concern, companies making the shortcuts may end up paying the price of a bad headline, in a collision-course with stakeholder interests. In 2023, security-minded company Okta leaked source code, along with many others such as CircleCI, Slack, etc. The Types of Security Mechanisms
The opportunity using CDEs to deliver security via the Cloud make it efficient because, as mentioned previously, no installation is required, but also because:
- mechanisms are independent from the device’s operating system;
- they can be updated and monitored remotely;
- they are independent from the user’s location;
- they can be applied in an adaptive manner, for example based on the specific role and context of the user.
Regarding the type of security mechanisms that can be delivered, these are the typical ones:
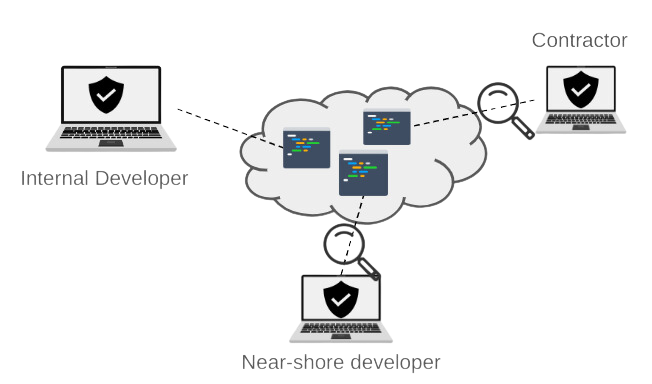
- Provide a centralized access to all the organization resources such that access can be monitored continuously.
- Centralized access enables the organization to take control of all the credentials for these resources, i.e. in a way that users do not have direct access to them (see this article for details about credentials protection),
- Implement data loss prevention measures via the applications used by developers such as the IDE (i.e. code editor), code repository applications, etc.
- Enable real-time observability of the entire workforce, via the inspection of logs using a SIEM application.
Realize Secure Software Development Best-Practices with Secure CDEs
We explained that the use of secure cloud development environments jointly benefits both the productivity and the security of the development process.
From a productivity standpoint, there's a lot to gain from the centralized management opportunity that the use of a secure CDE platform provides.
From a security perspective, delivering security mechanisms via the Cloud brings a load of benefits that transcend the hardware used across the developers to participate in the development process. In other words, the virtualization of development environment delivery is an enabler to foster the efficiency of a series of maintenance and security operations that are performed locally. It brings security for software development and allows organizations to implement secure software development best-practices.
This also provides an opportunity to template process workflows in an effort to make both productivity and security more systematic, in addition to reducing the cost of managing a development workforce.
If you are interested in understanding more the difference in architecture between a CDE platform and a secure CDE platform, read this additional article. All material in this text can be shared and cited with appropriate credits. For more information about our platform, please contact us at hello@strong.network