Enabling GenAI for Coding in Organizations
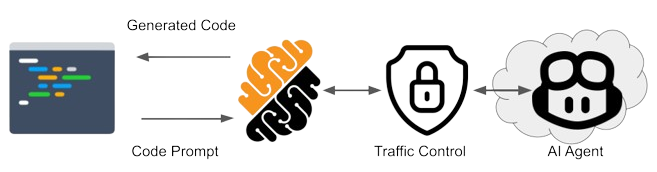
In this article, we explore how Secure Cloud Development Environments (CDE) enable building a robust, scalable, and efficient AI-driven infrastructure for developers that prioritizes compliance, monitoring, performance, feedback, and scalability. Secure CDEs help gain a deep understanding, control, and observability of the data exchange process between the development environment and an AI agent used to generate code. By leveraging a data access proxy, they enable secure and controlled access from CDEs to data resources, as well as governing data traffic between developers and the AI module so that the benefits listed above can be realized. Why Organizations Should Leverage AI for Application Development
What are the Benefits Around Productivity and Security?
Generative AI brings significant productivity benefits to code development by automating repetitive tasks, providing intelligent code suggestions, and enhancing the overall development workflow. By leveraging AI-powered code completion tools, developers can quickly write and debug code, reducing the time spent on mundane coding activities.
Generative AI can also assist in generating boilerplate code, creating documentation, and refactoring existing code, allowing developers to focus on more complex and creative aspects of software development. Furthermore, AI-driven insights and recommendations can help optimize code performance and ensure best practices, leading to higher quality software with fewer bugs. Overvall, it accelerates development cycles and enhances collaboration among development teams by providing consistent coding standards and reducing the cognitive load on individual developers.
When Gen AI-Assisted Coding is a Threat
One of the foremost concerns is data privacy and security. When using external AI agents, sensitive source code and proprietary information must be shared with third-party providers. This exposes the organization to risks of data breaches, unauthorized access, and intellectual property theft, in addition to complicating compliance efforts because regulations such as GDPR mandate strict controls over data access and processing.
AI-generated code might not always meet the organization’s quality and security standards. External AI agents may lack context-specific knowledge of the organization’s coding practices, leading to inconsistent code quality. Moreover, AI models can inadvertently introduce vulnerabilities or propagate existing ones, compromising the reliability and security of the software.
Finally, relying on external AI agents creates a dependency on third-party providers. This can lead to issues with service continuity, especially if the provider faces downtime, discontinuation of services, or goes out of business. Additionally, organizations might find it challenging to switch providers due to compatibility issues and the proprietary nature of AI model
Four Reasons Why Secure CDEs are Key Enablers for GenAI Coding
Deploy Developer Tooling at Scale
Deploying developer tooling at scale is a critical advantage of CDEs. In traditional development setups, each developer might need to manually configure their environment, leading to inconsistencies and potential setup errors.
CDEs provide pre-configured, standardized environments that can be deployed instantly across the entire development team using a container definition such as the one in the figure below. This approach ensures that all developers are working in identical environments, each configured to enforce access to compliant AI modules. In addition, such infrastructure allows organizations to pre-configure access to multiple AI modules in order to implement a resilient service.
Authenticated and authorized AI Access
Ensuring authenticated and authorized AI access is fundamental to secure development. The Secure CDE’s data access proxy ensures proper authentication to the right AI components, and verifies that users have proper authorization to use it. This configuration is illustrated in the next figure.
This combination of secure, credentials-safe authentication and precise authorization ensures that only legitimate users can access and interact with AI resources, minimizing the risk of accidental or malicious misuse. Control for All AI-Data Flows
Secure CDEs offer unparalleled control over AI-data flows, including both prompts and generated responses. Control is also needed on data entering the environment, such that potentially unwanted data intrusion can be detected. Equipped with a data access proxy, Secure CDEs can monitor and regulate the interaction between developers and AI models, ensuring that data is used appropriately and securely. This control is crucial for maintaining data privacy and security, as it allows organizations to track the origin and destination of data within the development environment. It is also crucial for security purposes: for example a potential vulnerable code generated by an AI can be intercepted before being merged into the source code. In all, by having a centralized mechanism to oversee AI-data flows, organizations can implement policies that prevent data misuse, ensure compliance with regulations, and provide transparency in AI operations.
Single Viewpoint for Observability
A single viewpoint for observability is essential for maintaining an efficient and secure development process. CDEs provide comprehensive data flow observability by centralizing traffic into a single interface, i.e the data access proxy. This unified view allows development and operations teams to quickly identify and address issues, monitor performance, and ensure compliance with security policies. This approach enhances detection and response to incidents in real-time and supports long-term analysis of the development process.
Conclusion
In conclusion, by leveraging a data access proxy, Secure CDEs ensure secure and controlled access to data resources, facilitating a comprehensive understanding and observability of the data exchange process.
Organizations should leverage AI for application development due to its significant productivity benefits, including automation of repetitive tasks, intelligent code suggestions, and enhanced workflow efficiency. Generative AI accelerates development cycles, improves code quality, and supports consistent coding standards, ultimately boosting collaboration among development teams.
However, the use of Generative AI, particularly with external AI agents, introduces risks such as data breaches, compliance challenges, inconsistent code quality, and dependency on third-party providers. These threats underscore the importance of secure, authenticated, and authorized AI access using a Secure CDE platform.
Secure CDEs provide key enablers for GenAI coding by allowing scalable deployment of developer tools, ensuring authenticated and authorized AI access, offering control over AI-data flows, and providing a central viewpoint for observability. By integrating these features, A Secure CDE platform enhances both productivity and security, empowering organizations to innovate while maintaining rigorous data protection and compliance standards.
All material in this text can be shared and cited with appropriate credits. For more information about our platform, please contact us at hello@strong.network