Remote Developers Are Part of the Liquid Workforce
The concept of a liquid workforce (see Forbes, Banco Santander, etc) is mostly about that, a part of the workforce is not permanent and can be adapted to dynamic market conditions. In short, in a liquid workforce a proportion of the staff is made of freelancers, contractors and other non permanent employees. Today, it is reported that about 20% of an IT workforce, including software developers, is liquid in a significant part of the Fortune 500 companies. Actually, working as a freelancer has been a common practice in the media and entertainment industry for a long time. This model is catching up today in many other industries. From the gig economy, to the increasing sentiment stemming from Gen-Y and Gen-Z’ers that employment should be flexible, multiple catalysts are contributing to the idea that the liquid approach is likely to continue eroding the classic workforce.
For corporations, this is actually a “perfect storm” that can be put to good use to adapt to increasingly faster changing market conditions. Indeed, the acceleration of the pace of technology and the issue for corporations to maintain a skill set that enables them to be competitive can be tackled by embracing this concept.
Remote Software Development in Startups and SMEs
In practice today, more SMEs and startups actually outsourced parts or sometimes most of its software development workforce.
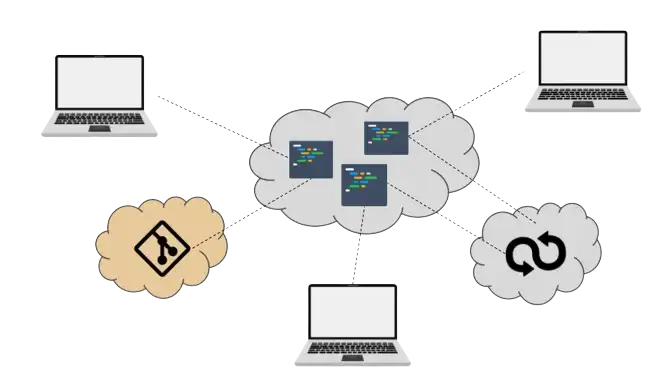
A key enabler to onboarding a liquid workforce is the democratization, in the world of application development and data science, of the use of only cloud-based infrastructure components (GitHub, GitLab, data buckets, etc) to manage source code and data. Expectedly, this opens to the possibility for (permanent and ephemeral) workforce’s members to work from anywhere because the corporate infrastructure is indeed, available anywhere. The use of Cloud Development Environments are part of this trend and provide a mechanism to onboard developers across the globe on pre-installed environments. Younger companies are adopting new types of tools and infrastructure faster than corporations and can then be more flexible with regard to enabling remote data access. Therefore the rise of the liquid workforce is more likely to be a bottom-up initiative across the industry in terms of company size.
In addition there are hundreds of companies situated in countries where labor cost and skill sets are combined advantageously that provide access to a liquid workforce.
Today, IT business process outsourcing and external application development are all together an USD 92 billion market. If you are openly eager to hire external help on LinkedIn, you will get contacted several times by boutique outsourcing partners, mostly from the Balkans or Asia. Consumers of these services really span the entire set of corporation sizes, across all industries. I have talked to a dozen of these service companies and sadly, very few have a clear plan of how to effectively protect the data of their customers. Most protective mechanisms hover around legal paperwork. Albeit this approach might be comforting for large corporations, this is mostly a sham for any smaller business settings that cannot really afford to take legal action, let alone in an international context.
How to Secure Development When Using Remote Developers
Unsurprisingly digital trust has to catch up with the liquid IT phenomenon. In practice, there are three simple measures that companies of all sizes can put in place to infuse a good sense of security. Ease of adoption is directly dependent on how these measures can be delivered, i.e. cost-effectively and with a minimal impact on operations.
The number one measure is to automate and streamline the onboarding process. In the domain of code development and data science where the set of necessary software components to enable productivity is quite significant, this is a tricky issue. Hence a performant and economically efficient onboarding mechanism to bring on liquid contributors has to be put in place first. I mentioned the use of Cloud Development Environments as an enabler for that.
Once on board, the number two measure is to ensure continuous data protection. This is another thorny issue because of the lack of classic corporate IT perimeter. Yet, as I explained previously, the Cloud is an efficient medium to allow remote access. From a security perspective, public and private clouds, e.g. Google GCP, AWS and Azure have reached a level of security that keeps most small-time cybercriminals and script kiddies ashore. In effect, this has migrated the attack surface for hackers to the network’s edges. In other words, the danger around data leaks becomes mostly confined around data access points and the developer’s behavior at each endpoint of the network rather than a centralized Cloud storage problem. Here, Secure Cloud Development Environments are the key enabler for protecting data on “the edge” of the development process. 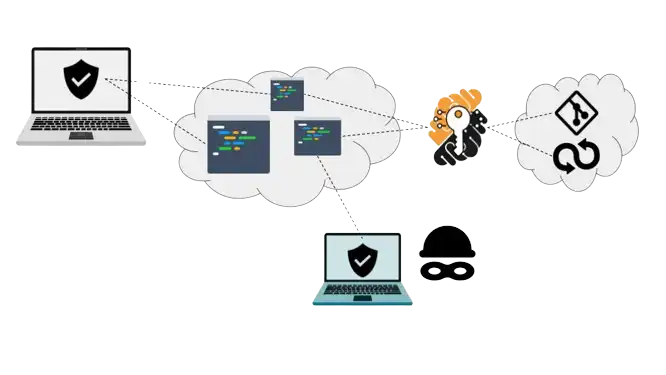
Putting it simply, it used to be that your internal servers might be targeted. Now, with a Cloud-based IT infrastructure, it’s mostly your endpoints, i.e. the developers’ laptops that are prey. Indeed in practice it is much easier to steal a laptop than hacking Google. In addition, malicious employee activities, aka insider threats around intellectual property theft such as source code and data are now becoming one of the growing concerns for corporations. This seems to be an outcome of embracing a liquid workforce (too naively), i.e. liquidity seems to erode some employees’ ethics as well! Finally the number three measure is setting up a continuous and adaptive audit system that enables the collection of security and compliance events across the entire Cloud-based infrastructure, including in particular its edges. Compliance with information security standards such an ISO 27001 (in particular the appendices) and SOC-2 is a starting point to set up a minimally sufficient protection program. As I mentioned above, technologies such as zero trust access control and data loss prevention, in particular cloud-delivered are some of the mechanisms that are contributing to enabling the secure liquid workforce. Because Secure Cloud Development Environments are accessed online, creating an audit trail is quite simple. Logs can be centrally collected with little effort and plugged in a SIEM tool.
How to Address Data Protection Challenges When Using Remote Developers
The shift towards a more flexible development workforce necessitates an innovative approach to digital trust to onboard remote developers securely. Companies can bolster security and facilitate this transition by implementing three key measures: (1) streamlining the onboarding process, (2) ensuring continuous data protection, and (3) establishing a robust audit system.
First, leveraging the trend of coding online using Cloud Development Environments simplifies the complex onboarding process for developers and data scientists, making it economically viable and efficient. You can learn more about the way to onboard remote developers in this 2023 DevOpPro Europe presentation. This approach is crucial for seamlessly integrating developers into the workflow. Second, the transition to cloud-based IT infrastructure has shifted the focus to securing data at access points and monitoring endpoint behaviors, as cloud platforms like GCP, AWS, and Azure already offer strong defenses against common cyber threats. Here, secure Cloud Development Environments are instrumental in safeguarding remote data on the network's edge, addressing the nuanced challenges presented by a dispersed workforce. Finally, as organizations navigate the complexities of integrating securely remote developers, these measures offer a roadmap to securing digital assets while accommodating the needs and dynamics of modern IT practices. The shift towards cloud-based solutions and the strategic implementation of security measures underscore the evolution of digital trust in tandem with the liquid IT phenomenon, ensuring that productivity, security, and compliance can be balanced.
All material in this text can be shared and cited with appropriate credits. For more information about our platform, please contact us at hello@strong.network