Webinar Transcript:
Laurent's Journey from Strong Codes to Strong Network
We observed Gitpod's approach and thought it was interesting but lacked a crucial element: security. We asked ourselves why we would replace traditional laptops with this online system. The key for us was adding security mechanisms to these online containers, combining data protection and IT efficiency to enhance what we're doing.
That was Laurent Balmelli, a cybersecurity expert with a PhD, talking about what the future of developing environments could be. Laurent was born in Switzerland but is truly a global citizen, having lived in many places like New York and Tokyo. Laurent's cybersecurity journey started with IBM before he left to found his own company, Strong Codes. Strong Codes was a startup that worked on preventing people from being able to reverse-engineer compiled applications by obfuscating and scrambling the source code.
That startup was acquired by Snapchat, which Laurent worked for briefly before he left to create his own company again, this time Strong Network. Strong Network is a cloud IDE, but also so much more. It's rethinking secure development environments for the modern era. In this episode, we get to sit down with Laurent and talk about development environments, how it's moving to the cloud, and what are the security risks of this. But before we get into that, it's time now to have a look at our Breach of the Week.
Atlassian Breach: Employee Credentials and Third-Party Risks
In the theme of development companies, today's breach we're looking at is Atlassian, because on Friday the 17th of February, Atlassian reportedly suffered a fairly significant breach due to third-party integration. As reported by Cyberscoop, employee credentials were stolen that gave access to a third party, in this case, Envoy. Now what is apparent is that all the data that was breached is actually from Atlassian's own employees.
Atlassian has claimed to have about 8,000 employees, although the breach has been said to be concerning 13,000 different people. This may be because Atlassian actually has a lot more people working for them, or the more likely scenario is that it contains records of employees who are no longer working with the company. So how does all this happen? Well, employee credentials are used all the time by attackers, and there are numerous ways in which they can get them. Of course, the favorite is through a phishing campaign, which still is on trend even in 2023. But there are also different ways that you can obtain a user's employee credential. The dark web and more recently dark telegram channels are a favorite for attackers to be able to sell and also buy these types of credentials. This has been an interesting separation of attackers in recent years. You have some attackers that specialize in targeted campaigns like phishing to try and find employee credentials. They will also search on public resources like docker images, other containers, or through source code to be able to obtain this information.
Exploiting Tools: The Rise of Credential-Based Cyber Attacks
And then if they don't want to use it, they can on-sell it to a new level of hackers who specialize in exploiting specific companies. This marketplace isn't entirely new, but it's definitely growing and could possibly have been how initial access was gained here. But it does show the trend in hacking activity that we're on right now. And that is that credentials are nearly used in all attacks, whether they're for initial access, whether they're used to elevate privileges. And the other thing we know is that developer accounts for developer tooling are becoming increasingly hot targets.
This is because developers, DevOps teams, and other engineers are really the gatekeepers to the information that the attackers want. So what does this mean for Atlassian? The biggest risk for Atlassian is that the attackers use this employee information to launch more sophisticated spear phishing and phishing campaigns on their employees to try and gain access deeper into their systems. At the moment, that seems fairly unlikely. The reason is that the attacker has already announced that the breach has been made.
Something that is typically done once an attacker has really leveraged as far as they can go with the resources, time, or really commitment that they have. The hacking group in question here named Sagesect seems to me reminiscent of other hacking groups like Lapsu$ with a younger following where the main goal seems to be notoriety rather than financial benefit. But the one thing that we can all learn from these types of attacks is that we need to start implementing areas of zero trust around all segments of our infrastructure and third-party services.
This includes adding multi-factor authentication and limiting IP addresses and access where possible. And of course, it may seem like an early 2000s technique, but using firewalls. But even then, we can't always be certain that our employees will do the right thing. That is why this conversation with Laurent today is on such a good topic. We're going to talk about securing the modern development environment. We're used to our integrated development environments, IDEs like Visual Studio Code or Atom.
They combined various tools that allow developers to do their tasks more efficiently. But like all things moving to the cloud and out of our control, IDEs are also heading that way. Big names like GitHub have launched their cloud IDEs like GitHub Codespaces as well as various other vendors.
But what does this mean for security?
Well, Laurent is working on a lot more than just a cloud IDE. Strong Network is looking at how they can make the entire development environment completely secure and also remote, suitable for a modern startup where, let's face it, we're all continuing to be remote and outside a lot of the parameters that organizations can control. So without further ado, here is the conversation between myself, Laurent Balmelli, and Dwayne McDaniel. Securing Cloud Development: The Evolution of Cloud IDEs
Welcome to the show, Laurent. Let's dive straight into the topic of cloud-integrated development environments (IDEs). We're seeing a shift in the development process to online platforms through browsers. How is this impacting the general landscape and particularly security for developers?
First, let's clarify what a cloud IDE is. It's an IDE running in a browser, but this definition doesn't fully capture what solutions like ours offer. It's more than just a cloud IDE; it's about managing containers online. In the DevOps process, containers are crucial for managing dependencies in your development environment. By hosting these containers online, you reduce the hassle of local commands and enhance security by keeping data online, away from developers' laptops.
You can access these online containers either through a cloud IDE, which facilitates remote interaction and authoring of information like source code, or through local IDEs connected remotely to these containers. This setup, known as remote development, is supported by tools like VS Code and JetBrains Gateway. Our platform focuses on Cloud Development Environments (CDEs), where you work directly within these environments using a cloud IDE. This approach streamlines the DevOps process, reducing friction across development, testing, and production stages, leading to fewer bugs and changes. When we started Strong Network, we questioned the purpose of just replicating a laptop's functionality online. Our goal was to blend the security aspects of VDI and Desktop as a Service with the IT efficiency of online containers. We aimed to offer a solution that combines the best of both worlds: robust data protection mechanisms and the operational benefits of containerized development environments. Reimagining Dev Security: Integrating Infrastructure Protection
Thanks for your insights, Laurent. The shift to cloud IDEs and containerization is fascinating, especially from a security perspective. Often, the focus is on managing secrets in the development process, but you're emphasizing the broader aspect of data security. Could you elaborate on what specific measures you're implementing beyond containerization for security?
We focus on infrastructure security, a crucial distinction from code security. Our approach involves decoupling the hardware used in DevOps processes from the development environments. Unlike practices like DevSecOps, which are more about removing vulnerabilities from code, our solution involves removing data from DevOps laptops and controlling network access with firewall rules, similar to what cloud providers offer. Our security measures are designed to prevent data exfiltration and malware infiltration. This becomes particularly relevant in use cases where clients need to prevent the extraction or copying of code. We don't deal with vulnerabilities in the code itself, but rather with infrastructure security, which can be seen as a replacement for traditional video solutions.
I see the importance of this. Why the focus on securing infrastructure now? What are the risks involved?
The need for infrastructure security varies by industry. In sectors like finance and insurance, where regulation and compliance are crucial, securing infrastructure becomes vital. Given the recent major breaches in the telecom and banking sectors in Australia, there's a growing awareness of these risks. The industry needs to understand the risks associated with code sprawl and developers' machines being outside of control. Addressing these risks might involve introducing governance legislation to compel large organizations to adopt stricter security measures.
The debate about the necessity of securing infrastructure, particularly in the banking and financial sectors, is becoming increasingly significant. In these industries, failure to implement proper security measures can lead to severe consequences from compliance assessors or CIOs. Moreover, the recent breaches at companies like Nvidia and EA, where source code was compromised, highlight the importance of protecting intellectual property (IP).
In the gaming industry, for example, companies like Ubisoft are highly cautious about their source code security due to IP concerns. Beyond IP, the exposure of source code can also reveal vulnerabilities that can be exploited to breach systems and leak customer data. This risk extends across various industries, underscoring the need for robust security measures.
Traditionally, having a replica of source code on a developer's laptop was seen as the only option, despite its security risks. The alternative, using complex Virtual Desktop Infrastructure (VDI) systems, was often deemed too cumbersome and expensive. As a result, many technology companies opted to take the risk for the sake of agility.
However, the landscape is changing. The recent spate of source code hacks has led to a growing realization that source code is not benign information but something that needs to be protected. This awareness is pushing companies to reconsider their approach to security, recognizing that effective protection of their digital assets is not just a regulatory compliance issue but a crucial aspect of maintaining their competitive edge and safeguarding their customers.
Balancing Internal Security and Efficiency in DevOps
The recent security breaches by groups like Lapsu$ are indeed startling, especially considering that they targeted major companies with presumably strong security measures. The surprising element was the discovery that these breaches were orchestrated not by state actors but by a group of teenagers. What’s more alarming is the manner in which these breaches were executed. These teenagers didn't use sophisticated hacking methods; instead, they simply purchased access to source codes and development environments. They were openly recruiting insiders on Telegram, offering thousands of dollars for access to certain companies' development environments.
This situation is a stark reminder of the risks posed by internal threats. While companies often focus on external threats, internal risks, such as employees who might collaborate with external parties for personal gain, are equally dangerous. It only takes one individual in a vulnerable position to compromise the entire system.
This reality prompts a critical debate in the security community. Traditionally, security measures are designed to keep external bad actors out. However, we now face the challenge of addressing internal threats, requiring a shift in how we view and manage security within organizations. The question becomes: how restrictive and vigilant should companies be towards their own employees, acknowledging that they could potentially become threats? This debate is vital in shaping future security strategies, balancing the need for robust security with the trust and freedom necessary for a productive and positive work environment.
Absolutely, the discussion around insider threats is becoming increasingly relevant, especially in light of recent changes in work environments due to the pandemic. High turnover rates, potential grudges, and other factors play into this. But fundamentally, it's about maintaining good hygiene in terms of governance and process management. It's critical to know where your assets are. Just like how investors trust us with their money, we need to be diligent in managing our processes. If there’s an opportunity to improve governance and visibility, we should take it.
What we’re trying to do is combine the efficiency of containers online for optimal DevOps with robust security. These two aspects might seem conflicting initially, but what we’ve demonstrated is their ability to coexist and provide the best of both worlds. Implementing good hygiene in our code and development processes is a positive step.
Regarding insider threats, while there may be cases of ill-intentioned individuals, it’s not always the norm. I’ve had interactions with developers in Eastern Europe, particularly in places like Gdansk, Poland, where a common concern is remote developers juggling multiple jobs - sometimes more than two or three. While this might seem alarming, it’s important to note that it's not a widespread issue; it's more anecdotal. Most developers are respectful and professional. The key takeaway is that it's mostly about maintaining hygiene in our processes. If we can achieve a balance between efficient DevOps and strong security, we should definitely aim for that.
Enhancing DevOps with Governance-Focused Platforms
Discussing governance is intriguing, especially since platforms like Codespaces or Gitpod often overlook it. Your solution, however, seems to blend seamlessly into broader security and DevOps frameworks. It fosters a comprehensive organizational dialogue about governance, a subject typically not in the daily purview of many. Indeed, you're right. The critical question is who exactly should be concerned with governance? As a lifelong developer, I've always valued the need for a comfortable and efficient working environment that fosters productivity and creativity. However, when you transition into managerial or entrepreneurial roles, understanding and overseeing governance becomes crucial.
Our aim has always been to create a developer-first solution. Interestingly, the inception of our platform was for our own use. Oz and I initially developed it to streamline hiring and managing remote teams. This personal need led to the creation of a platform that is now beneficial for many others. The unique aspect of our solution is its context-aware security. It’s not a generic, one-size-fits-all approach. Instead, it adapts to the specific context, ensuring it doesn't hinder developers' work. For example, managing keys and credentials can be tedious for developers. Our solution automates this, removing a significant burden. It's about blending efficiency and security in a way that enhances, rather than disrupts, the developer experience. Cloud environments promise to make security more user-friendly, which is a significant advancement.
Indeed, platforms that facilitate secure development are crucial. We've covered a lot, from governance and compliance to legislation. As a developer, I'm paying close attention to this discussion, but usually, I wouldn’t dive into these topics.
As we grow and take on more responsibilities, our perspectives shift. For me, now with a family and stakeholders to report to, tools that help organize and govern are invaluable. It's not just about my work as a developer; it's about maintaining an overview of the entire process.
Exactly, and if these tools don’t disrupt my workflow as a developer, it’s a win-win situation.
Absolutely. Our approach is about seamless integration. For instance, GitHub's ecosystem already captures a lot of process data. Governance isn’t just about one tool; it's about combining various tools to oversee the entire development process efficiently. Our platform aligns with this approach, enhancing what already exists in the ecosystem.
Charting the Evolution of Secure Cloud-Based Development
As we conclude, it's clear this conversation is far from over. Laurent, your insights have been enlightening. For those wanting to delve deeper into these topics, where can they find your articles and contributions to the security dialogue?
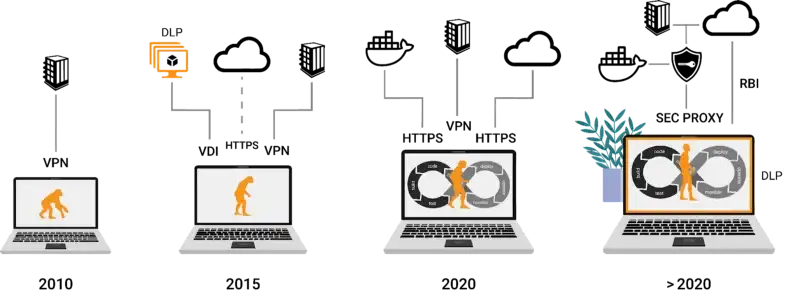
Our website, Strong Network, is a great starting point for blogs and webinars. I’ve also contributed a series of webinars and articles on Medium, discussing security and our work at Strong Network. One recent piece, ‘The Virtual Secure Developer Laptop,’ encapsulates much of what we discussed today. It explores replacing traditional secure developer environments with more flexible, cloud-based solutions. Yeah, that article is fantastic. There's an illustration in there that I absolutely loved – a timeline of the computer evolution. It's one of those moments, like when you use the Wayback Machine, where you can look at it and think, "Oh, my God, I get it now. This makes so much sense of how far we've come."
Thank you. It's incredible to think it was only 10 years ago. Look at how far we've come in that time. Back then, we stored everything previously on our laptops because there weren't many cloud applications. But now, everything has migrated to the cloud. The last step is the developer's information, source code, and data. Everything else has already moved to the cloud, including CRM data. In 2008, people thought putting customer data on the cloud was crazy, but now everyone does it. It's fascinating.
Well, Laurent, I want to take this opportunity to thank you once more for joining us on our Gitguardian Secure Repo. It's been a captivating conversation, and I hope we can revisit this topic in the future. To our audience, thank you for tuning in. Be sure to check out the articles Laurent mentioned; they provide valuable insights into the direction we're heading. Laurent, thanks again, and I'll see you all next time. Explore the latest technological advancements in secure developer environments in our upcoming webinar. We'll discuss essential strategies for securing the development process and introduce innovative solutions to protect your enterprise's development structure.
All material in this text can be shared and cited with appropriate credits. For more information about our platform, please contact us at hello@strong.network