How to Work with Remote Teams with Secure CDEs
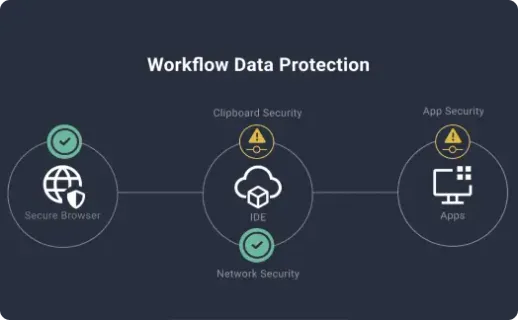
Secure Cloud Development Environments (CDEs) have transformed software development, especially for organization facing challenges in remote collaboration settings. I explain here how these environments secure and streamline collaboration across geographically dispersed teams and allow organization to save costs.
Read more
12/02/2024